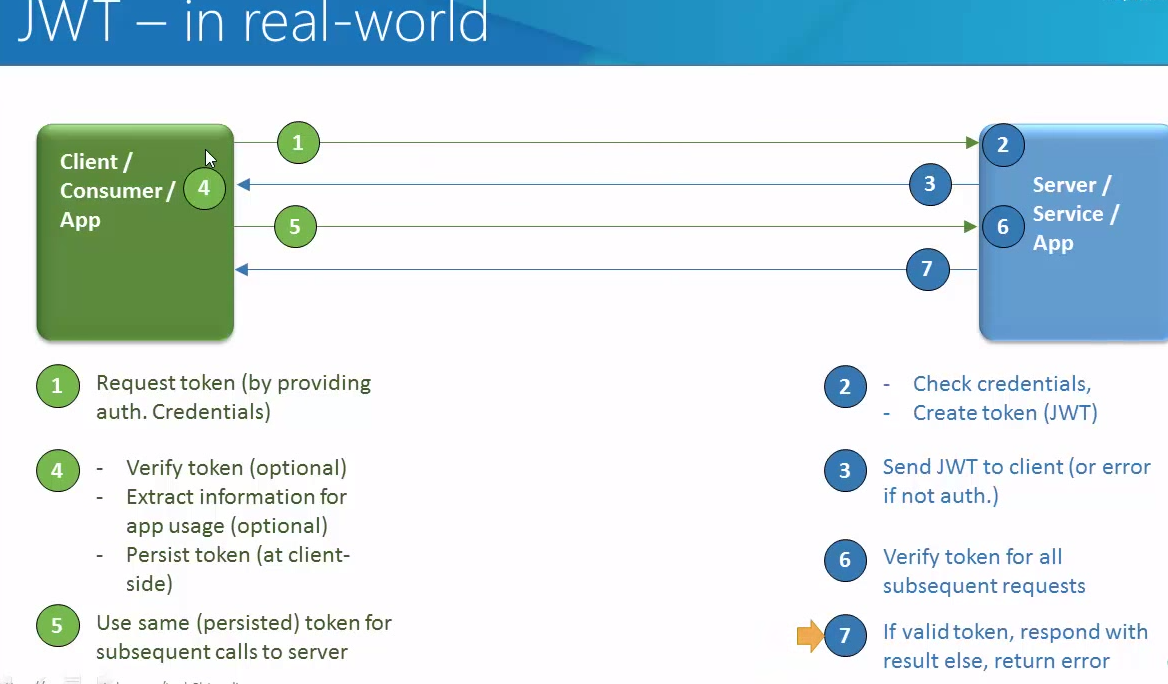
As mentioned in my previous post about Application container cloud. We can use two options to upload application archive to ACSS
- UI console (Already covered in previous post)
- From Stroge cloud service via REST API
In this post, we will talk about upload archive via storage cloud Service using REST API. There is two steps for that
- Store archive to Storage Cloud service.
- Deploy Archive to ACCS.
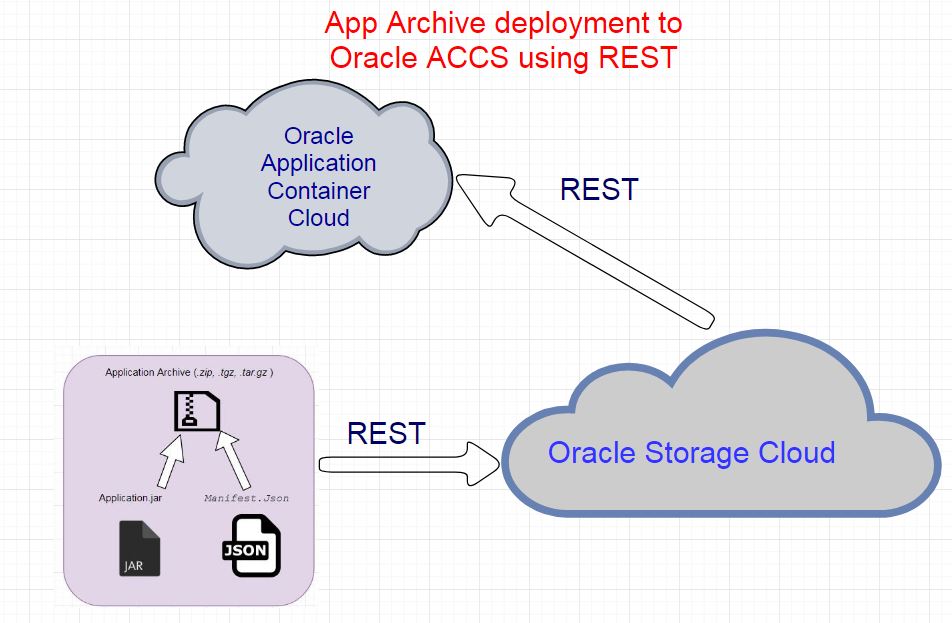
Information credentials for cloud account should be handy as identity, domain, password for using in REST API. Using cURL scripts to upload your application to the storage service.
Note : cURL is a tool to transfer data from or to a server, using one of the supported protocols (DICT, FILE, FTP, FTPS, GOPHER, HTTP, HTTPS, IMAP, IMAPS, LDAP, LDAPS, POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMB, SMBS, SMTP, SMTPS, TELNET and TFTP.
Store archive to Storage Cloud service
Before uploading in Storage cloud, We need to build container in Storage Cloud Service. Either you can via Storage cloud UI console. Building using UI console is pretty easy and straightforward.
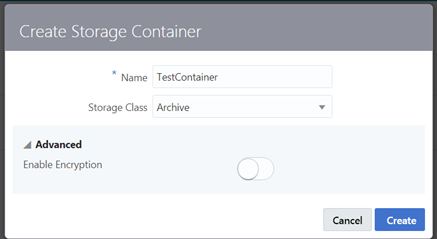
We will create container via curl command.
-
Below Script will create storage container.
# CREATE STORAGE CONTAINER curl -i -X PUT \ -u User-Name:Password \ https://hostname/v1/Storage-Identity-Domain/App-Name
-
Now upload your application archive to the storage container.
# PUT ARCHIVE IN STORAGE CONTAINER curl -i -X PUT \-u User-Name:Password \ https://hostname/v1/Storage-Identity-Domain/App-Name/Archive-File-Name -T Path-to-local-file/Archive-File-Name
For example use following script to upload it
curl -i -X PUT \ -u sampleUserName:samplePassword \ https://storage.oraclecloud.com/v1/Storagecontainer/DeveloperSkillsApp/SpringBootJpaDev-1.0-dist.zip -T target/SpringBootJpaDev-1.0-dist.zip
After running these script, it is uploaded to Storage cloud container.
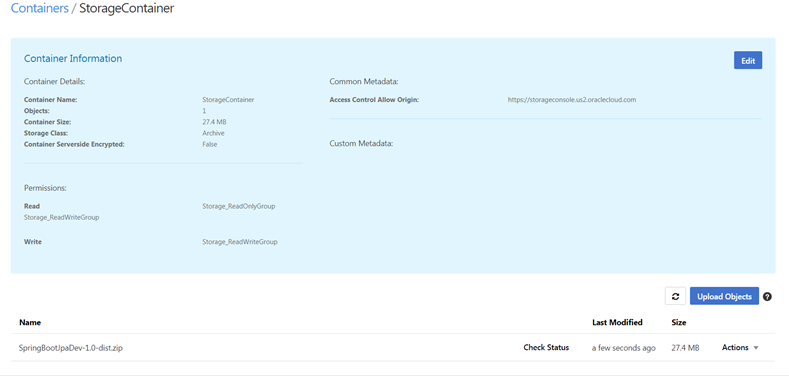
Deploy Archive to ACCS –
After uploading archive to Storage cloud servicee, ACC’s deployment procedure can be invoked. We need to provide standard set of information while deploying. Sample schema of script should be as follows
# Mock Deployment Script
url -i -X POST \
-u User-Name:Password \
-H "X-ID-TENANT-NAME:Identity-Domain" \
-H "Content-Type: multipart/form-data" \
-F "name=App-Name" \
-F "runtime=java" \
-F "subscription=Monthly" \
-F "[email protected]" \
-F "archiveURL=App-name/Archive-File-Name" \
-F "notes=Your Notes here" \
https://hostname/paas/service/apaas/api/v1.1/apps/Identity-Domain
Trying to upload with following script –
curl -v -u "USERNAME:PASSWORD” -X POST -H "X-ID-TENANT-NAME: IDENTITY_DOMAIN" -H "Content-Type: multipart/form-data" -F "name=Developer-skills-service" -F "runtime=java" -F "subscription=Monthly" -F "archiveURL= Storagecontainer/SpringBootJpaDev-1.0-dist.zip " -F "notes=Developer Skills Service Deployment" https://apaas.REGION.oraclecloud.com/paas/service/apaas/api/v1.1/apps/IDENTITY_DOMAIN
When you deploy your application, you can reference a deployment.json file. Information about deployment like memory , instances etc. can be pass via deployment.json.
You can automate these two process using maven. You can also configured this by maven plugin in Oracle Developer cloud services.
That’s all for now. Happy Oracle Cloud learning.